Nos aparecerá el siguiente código indicándonos que el equipo con IP 172.26.103.8 tiene todos los puertos abiertos.
kdesu -n /usr/bin/nmap -T Normal -O 172.26.103.8 > /tmp/kde-alumno/knmap_stderr_1017100316 2> /tmp/kde-alumno/knmap_stderr_1385659310
Starting Nmap 4.20 ( http://insecure.org ) at 2008-04-25 09:31 CEST
Interesting ports on 172.26.103.8:
Not shown: 1694 closed ports
PORT STATE SERVICE
53/tcp open domain
111/tcp open rpcbind
10000/tcp open snet-sensor-mgmt
MAC Address: 00:0F:EA:31:C5:FA (Giga-Byte Technology Co.)
No exact OS matches for host (If you know what OS is running on it, see http://insecure.org/nmap/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=4.20%D=4/25%OT=53%CT=1%CU=33247%PV=Y%DS=1%G=Y%M=000FEA%TM=481188E
OS:0%P=i686-pc-linux-gnu)SEQ(SP=D8%GCD=1%ISR=EF%TI=Z%II=I%TS=8)SEQ(SP=D8%GC
OS:D=2%ISR=EF%TI=Z%II=I%TS=8)SEQ(SP=D8%GCD=1%ISR=EF%TI=Z%II=I%TS=8)OPS(O1=M
OS:5B4ST11NW4%O2=M5B4ST11NW4%O3=M5B4NNT11NW4%O4=M5B4ST11NW4%O5=M5B4ST11NW4%
OS:O6=M5B4ST11)WIN(W1=16A0%W2=16A0%W3=16A0%W4=16A0%W5=16A0%W6=16A0)ECN(R=Y%
OS:DF=Y%T=40%W=16D0%O=M5B4NNSNW4%CC=N%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%RD=
OS:0%Q=)T2(R=N)T3(R=Y%DF=Y%T=40%W=16A0%S=O%A=S+%F=AS%O=M5B4ST11NW4%RD=0%Q=)
OS:T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S
OS:+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=
OS:Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=40%TOS=C0%IPL=164%UN=0
OS:%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUL=G%RUD=G)IE(R=Y%DFI=N%T=40%TOSI=S%CD=S%S
OS:I=S%DLI=S)
Uptime: 0.030 days (since Fri Apr 25 08:49:08 2008)
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at http://insecure.org/nmap/submit/ .
Nmap finished: 1 IP address (1 host up) scanned in 11.862 seconds
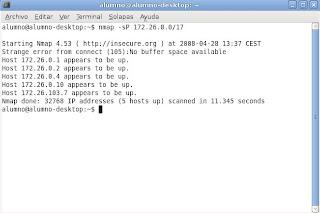
Starting Nmap 4.53 ( http://insecure.org ) at 2008-04-28 13:37 CEST
Strange error from connect (105):No buffer space available
Host 172.26.0.1 appears to be up.
Host 172.26.0.2 appears to be up.
Host 172.26.0.4 appears to be up.
Host 172.26.0.10 appears to be up.
Host 172.26.103.7 appears to be up.
Nmap done: 32768 IP addresses (5 hosts up) scanned in 11.345 seconds .
4 ¿Cuáles son los ordenadores de nuestra clase que están encendidos?
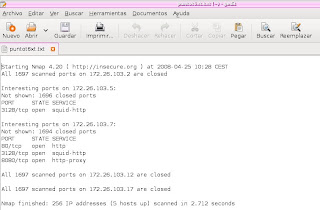
Nos aparecerá algo similar al código que añado:
Starting Nmap 4.20 ( http://insecure.org ) at 2008-04-25 10:28 CEST
All 1697 scanned ports on 172.26.103.2 are closed
Interesting ports on 172.26.103.5:
Not shown: 1696 closed ports
PORT STATE SERVICE
3128/tcp open squid-http
Interesting ports on 172.26.103.7:
Not shown: 1694 closed ports
PORT STATE SERVICE
80/tcp open http
3128/tcp open squid-http
8080/tcp open http-proxy
All 1697 scanned ports on 172.26.103.12 are closed
All 1697 scanned ports on 172.26.103.17 are closed
Nmap finished: 256 IP addresses (5 hosts up) scanned in 2.712 seconds
5 Averiguar si el equipo con IP 127.26.103.9 está jugando a los Worms.
Starting Nmap 4.53 ( http://insecure.org ) at 2008-04-29 09:47 CEST
Interesting ports on 172.26.103.20:
PORT STATE SERVICE
17010/udp open|filtered unknown
17012/udp open|filtered unknown
MAC Address: 00:0F:EA:31:C5:FA (Giga-Byte Technology Co.)
Nmap done: 1 IP address (1 host up) scanned in 1.597 seconds
A continuación averiguaremos qué equipos están jugando en red escribiendo el siguiente comando en la terminal: sudo nmap -sU -p 17010,17012 172.26.103.0/24.
El resultado será el siguiente:
Starting Nmap 4.53 ( http://insecure.org ) at 2008-04-29 10:04 CEST
Interesting ports on 172.26.103.2:
PORT STATE SERVICE
17010/udp closed unknown
17012/udp closed unknown
MAC Address: 00:1A:4D:6E:07:EB (Gigabyte Technology Co.)
Interesting ports on 172.26.103.5:
PORT STATE SERVICE
17010/udp closed unknown
17012/udp closed unknown
MAC Address: 00:1A:4D:7F:9D:D3 (Gigabyte Technology Co.)
Interesting ports on 172.26.103.7:
PORT STATE SERVICE
17010/udp closed unknown
17012/udp closed unknown
Interesting ports on 172.26.103.8:
PORT STATE SERVICE
17010/udp closed unknown
17012/udp closed unknown
MAC Address: 00:1A:4D:75:71:79 (Gigabyte Technology Co.)
Interesting ports on 172.26.103.9:
PORT STATE SERVICE
17010/udp closed unknown
17012/udp closed unknown
MAC Address: 00:1A:4D:75:70:74 (Gigabyte Technology Co.)
Interesting ports on 172.26.103.12:
PORT STATE SERVICE
17010/udp closed unknown
17012/udp closed unknown
MAC Address: 00:C0:9F:F2:ED:63 (Quanta Computer)
Interesting ports on 172.26.103.13:
PORT STATE SERVICE
17010/udp open|filtered unknown
17012/udp open|filtered unknown
MAC Address: 00:16:17:4F:AF:D5 (MSI)
Interesting ports on 172.26.103.17:
PORT STATE SERVICE
17010/udp closed unknown
17012/udp closed unknown
MAC Address: 00:1B:38:AB:BE:A2 (Compal Information (kunshan) CO.)
Interesting ports on 172.26.103.20:
PORT STATE SERVICE
17010/udp open|filtered unknown
17012/udp open|filtered unknown
MAC Address: 00:0F:EA:31:C5:FA (Giga-Byte Technology Co.)
Interesting ports on 172.26.103.26:
PORT STATE SERVICE
17010/udp closed unknown
17012/udp closed unknown
MAC Address: 00:19:66:44:E6:F3 (Asiarock Technology Limited)
Interesting ports on 172.26.103.28:
PORT STATE SERVICE
17010/udp closed unknown
17012/udp closed unknown
MAC Address: 00:1A:4D:75:70:94 (Gigabyte Technology Co.)
Nmap done: 256 IP addresses (11 hosts up) scanned in 3.142 seconds
Los puertos del WOW son 6112, 3724, 6881-6999.
A continuación averiguaremos los equipos de la red que están jugando al WOW, para ello pondremos en la terminal: sudo nmap -sU -p 6112,3724,6881-6999 172.26.103.0/24.
All 121 scanned ports on 172.26.103.2 are closed
MAC Address: 00:1A:4D:6E:07:EB (Gigabyte Technology Co.)
All 121 scanned ports on 172.26.103.5 are closed
MAC Address: 00:1A:4D:7F:9D:D3 (Gigabyte Technology Co.)
All 121 scanned ports on 172.26.103.7 are closed
All 121 scanned ports on 172.26.103.8 are closed
MAC Address: 00:1A:4D:75:71:79 (Gigabyte Technology Co.)
All 121 scanned ports on 172.26.103.9 are closed
MAC Address: 00:1A:4D:75:70:74 (Gigabyte Technology Co.)
All 121 scanned ports on 172.26.103.12 are closed
MAC Address: 00:C0:9F:F2:ED:63 (Quanta Computer)
All 121 scanned ports on 172.26.103.13 are open|filtered
MAC Address: 00:16:17:4F:AF:D5 (MSI)
All 121 scanned ports on 172.26.103.17 are closed
MAC Address: 00:1B:38:AB:BE:A2 (Compal Information (kunshan) CO.)
All 121 scanned ports on 172.26.103.20 are closed
MAC Address: 00:0F:EA:31:C5:FA (Giga-Byte Technology Co.)
All 121 scanned ports on 172.26.103.26 are closed
MAC Address: 00:19:66:44:E6:F3 (Asiarock Technology Limited)
All 121 scanned ports on 172.26.103.28 are closed
MAC Address: 00:1A:4D:75:70:94 (Gigabyte Technology Co.)
All 121 scanned ports on 172.26.103.33 are closed
MAC Address: 00:1A:92:55:DC:EF (Asustek Computer)
Nmap done: 256 IP addresses (12 hosts up) scanned in 233.499 seconds
Las líneas resultantes son:
Starting Nmap 4.53 ( http://insecure.org ) at 2008-04-29 10:16 CEST
Interesting ports on 172.26.103.2:
PORT STATE SERVICE
53/tcp closed domain
80/tcp closed http
Interesting ports on 172.26.103.5:
PORT STATE SERVICE
53/tcp closed domain
80/tcp closed http
Interesting ports on 172.26.103.7:
PORT STATE SERVICE
53/tcp closed domain
80/tcp closed http
Interesting ports on 172.26.103.8:
PORT STATE SERVICE
53/tcp closed domain
80/tcp closed http
Interesting ports on 172.26.103.9:
PORT STATE SERVICE
53/tcp closed domain
80/tcp closed http
Interesting ports on 172.26.103.12:
PORT STATE SERVICE
53/tcp closed domain
80/tcp closed http
Interesting ports on 172.26.103.17:
PORT STATE SERVICE
53/tcp closed domain
80/tcp closed http
Interesting ports on 172.26.103.20:
PORT STATE SERVICE
53/tcp closed domain
80/tcp open http
Interesting ports on 172.26.103.26:
PORT STATE SERVICE
53/tcp closed domain
80/tcp open http
Interesting ports on 172.26.103.28:
PORT STATE SERVICE
53/tcp closed domain
80/tcp closed http
Nmap done: 256 IP addresses (10 hosts up) scanned in 0.936 seconds)
Para averiguar los pc's encendidos de nuestra red pondremos nmap -sP 172.26.0.0/24.
Starting Nmap 4.53 ( http://insecure.org ) at 2008-04-29 08:58 CEST
Strange error from connect (105):No buffer space available
Host 172.26.0.1 appears to be up.
Host 172.26.0.2 appears to be up.
Host 172.26.0.4 appears to be up.
Host 172.26.0.10 appears to be up.
Host 172.26.103.2 appears to be up.
Host 172.26.103.7 appears to be up.
Host 172.26.103.20 appears to be up.
Nmap done: 32768 IP addresses (7 hosts up) scanned in 10.956 seconds
Para ver los puertos que tienen abiertos pondremos: nmap --allports 172.26.103.0/24 y el código resultante es:
Starting Nmap 4.53 ( http://insecure.org ) at 2008-04-29 09:37 CEST
All 1714 scanned ports on 172.26.103.2 are closed
Interesting ports on 172.26.103.3:
Not shown: 1711 closed ports
PORT STATE SERVICE
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Interesting ports on 172.26.103.5:
Not shown: 1713 closed ports
PORT STATE SERVICE
3128/tcp open squid-http
Interesting ports on 172.26.103.7:
Not shown: 1713 closed ports
PORT STATE SERVICE
902/tcp open iss-realsecure-sensor
All 1714 scanned ports on 172.26.103.8 are closed
Interesting ports on 172.26.103.9:
Not shown: 1713 closed ports
PORT STATE SERVICE
10000/tcp open snet-sensor-mgmt
All 1714 scanned ports on 172.26.103.12 are closed
All 1714 scanned ports on 172.26.103.17 are closed
Interesting ports on 172.26.103.20:
Not shown: 1710 closed ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
Interesting ports on 172.26.103.26:
Not shown: 1707 closed ports
PORT STATE SERVICE
80/tcp open http
111/tcp open rpcbind
139/tcp open netbios-ssn
445/tcp open microsoft-ds
2049/tcp open nfs
3128/tcp open squid-http
8080/tcp open http-proxy
Nmap done: 256 IP addresses (10 hosts up) scanned in 3.926 seconds



No hay comentarios:
Publicar un comentario